 |
| Cyber Periodic Table of 50 Enterprise Controls |
Saturday, September 17, 2016
Periodic Table of Enterprise CyberSecurity Controls
Saturday, July 30, 2016
80% of professionals say on-premisis security more mature than "cloud"
 |
| Courtesy Doug Cahill blog (ESG Research |
Any company selling SaaS will recognize this type of customer concern.
Of course the reality is that there is no one "cloud". Maturity and capability will vary across all organizations and industries. Unfortunately, many risk assessors mistake possession for security.
When assessing risk to adopt a SaaS product, consider..
Tuesday, July 19, 2016
Bit9 + Carbon Black + Confer
Cybersecurity vendor Carbon Black (formerly bit9) has announced acquisition today of malware detection upstart vendor Confer.
Confer is a lesser known advanced endpoint protection vendor. It provides a behavior-based method of threat detection.
There is no shortage of "next generation" behavior-based threat detection products, such as:
- Palo Alto Networks Traps (cyvera)
- SentinelOne
- CrowdStrike Falcon
Tuesday, June 21, 2016
Pure JS Ransomware
Different from the recent rash of malicious javascript files, this javascript does not rely on the introduction of a malicious binary. Sophos titled the malware "JS/Ransom-DDL".
This type of malware can be dangerous if you have never considered javascript as a possible attack vector. Without a binary to detect/inspect/observe, some advanced malware defense tools will be useless.
Monday, June 20, 2016
Remote Access Service GoToMyPC Compromise
According to Citrix, "GoToMYPC service has been targeted by a very sophisticated password attack."
Sophisticated or not - this should be a reminder to enterprises that consumer oriented remote-control applications cannot be ignored.
Sophisticated or not - this should be a reminder to enterprises that consumer oriented remote-control applications cannot be ignored.
Saturday, June 18, 2016
Gartner: Top 10 InfoSec Technologies for 2016
- Cloud Access Security Brokers
- Endpoint Detection and Response
- Nonsignature Approaches for Endpoint Prevention
- User and Entity Behavioral Analytics
- Microsegmentation and Flow Visibility
- Security Testing for DevOps (DevSecOps)
- Intelligence-Driven Security Operations Center Orchestration Solutions
- Remote Browser
- Deception
- Pervasive Trust Services
Monday, June 13, 2016
Microsoft + LinkedIn: Employee Privacy?
Today Microsoft announced it "will acquire LinkedIn for $196 per share in an all-cash transaction valued at approximately $26.2 billion."
LinkedIn is increasingly the means for employees to connect with new career opportunities. Microsoft increasingly represents Enterprise customers rather than individual consumers. What affect might this deal have on workplace privacy?
Friday, June 10, 2016
Google Chrome PDF Reader : Remote code execution
Do you avoid Adobe Reader and Acrobat due to the never-ending stream of security problems? Perhaps you have done away with PDF reader software all together in favor of the viewer included with Chrome?
If you have, you will be disappointed to learn that the Chrome viewer is vulnerable to a remote code execution vulnerability. The viewer included in Chrome, called PDFium, can be used run code of the attacker's choice.
If you have, you will be disappointed to learn that the Chrome viewer is vulnerable to a remote code execution vulnerability. The viewer included in Chrome, called PDFium, can be used run code of the attacker's choice.
Tuesday, June 7, 2016
2016 vs 2010 Magic Quadrant for Enterprise Firewalls
Gartner released the 2016 Magic Quadrant for Enterprise Firewalls almost two weeks ago.
The biggest surprise is how stratified Gartner views this market. There are two leaders, two challengers, and all other vendors tied for last-place.
What is going on?
The biggest surprise is how stratified Gartner views this market. There are two leaders, two challengers, and all other vendors tied for last-place.
What is going on?
Friday, May 27, 2016
Missing 2015 MS Office Patch targeted by APT actors
Computers running vulnerable versions of Microsoft Office (missing MS15-099) are actively
targeted by multiple advanced threat actors. Although this zero-day
attack was patched in September 2015, advanced attackers continue to exploiting
this vulnerability, suggesting widespread patching failures.
Kaspersky Labs compiled a list that included: Platinum, APT16, EvilPost, and SPIVY.
Kaspersky Labs compiled a list that included: Platinum, APT16, EvilPost, and SPIVY.
| Code-name | Researcher | Discovery date | Activity area | MS15-099 exploitation | Reference |
| Platinum | Microsoft | August 2015 (zero-day discovery) | India, Malaysia, Indonesia, China | Resume for technical position | PLATINUM: Targeted attacks in South and Southeast Asia, Windows Defender Advanced Threat Hunting Team |
| EvilPost | FireEye / Kaspersky | November 2015 | Japan | Japanese national defense topics | The EPS Awakens, Threat Research Blog |
| APT16 | FireEye | December 2015 | Taiwan, China | Taiwanese opposition party (Democratic Progressive Party) document | The EPS Awakens - Part 2, Threat Research Blog |
| SPIVY | Palo Alto Networks | March 2016 | Hong Kong | Hong Kong pro-democracy documents | New Poison Ivy RAT Variant Targets Hong Kong Pro-Democracy Activists |
| Danti | Kaspersky | March 2016 | India, Kazakhstan, Kyrgyzstan, Uzbekistan, Myanmar, Nepal, and Philippines | forged Indian government communication targeting Indian embassies in Hungary, Denmark, Colombia and Ministry of Foreign Affairs | CVE-2015-2545: overview of current threats, Danti attacks |
Thursday, May 26, 2016
CEO dismissed after successful phishing email
Australian aerospace firm FACC announced yesterday the immediate dismissal of CEO Walter Stephan.
“In the supervisory board meeting, held on May 24, 2016, Mr. Walter Stephan (CEO) was revoked by the supervisory board as chairman of the management board of FACC AG with immediate effect for important reason. The supervisory board came to the conclusion, that Mr. Walter Stephan has severely violated his duties, in particular in relation to the "Fake President Incident". Reuters confirms this is a reference to a successful phishing email. “The hoax email asked an employee to transfer money to an account for a fake acquisition project - a kind of scam known as a "fake president incident".”
Tuesday, May 24, 2016
Swiss defense contractor RUAG: APT breach findings
The attackers infiltrated the environment, established covert internal communication, staged hidden information stores, and coordinated hierarchical data exfiltration.
The Reporting and Analysis Center for Information Assurance (MELANI) provides both a summary and detailed version of findings.
RAUG Compromise
Locating the target
 “Vulnerable web servers on the Internet” were used as both watering holes and first-stage command-and-control. Sometimes disguised as Google analytics JavaScript, browsers are redirected to a
secondary infection site where victim IP addresses can be compared to the list
of intended targets.
“Vulnerable web servers on the Internet” were used as both watering holes and first-stage command-and-control. Sometimes disguised as Google analytics JavaScript, browsers are redirected to a
secondary infection site where victim IP addresses can be compared to the list
of intended targets. Infection happens in two stages. First "a system is infected by a reconnaissance malware." If the system is sufficiently interesting, "stage 2 malware is added, and ultimately persistence is gained."
Monday, May 23, 2016
Content management systems (CMS) insecurity
Content management systems continue lowering the bar for webmasters. According to a recent Secunia report, "over a third of the websites online are powered by four key platforms: WordPress, Joomla!, Drupal, and Magento."
Unfortunately, this "introduces a large influx of unskilled webmasters and service providers responsible for the deployment and administrations of these sites." Common disregard for system maintenance.
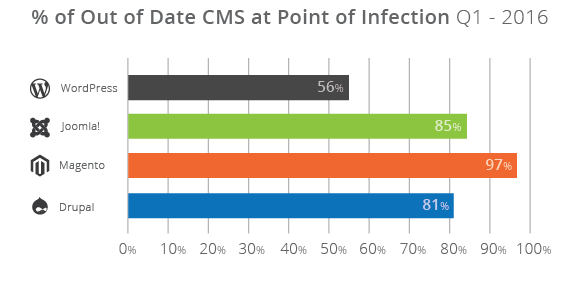 "As the technical aptitude required to have a website drops," the webmaster is increasingly the weakest link. Sites running atop the top 4 CMS platform investigated by Securi were overwhelmingly out-of-date.
"As the technical aptitude required to have a website drops," the webmaster is increasingly the weakest link. Sites running atop the top 4 CMS platform investigated by Securi were overwhelmingly out-of-date.
Source: Securi Website Hacked Report 2016 - Q1
Unfortunately, this "introduces a large influx of unskilled webmasters and service providers responsible for the deployment and administrations of these sites." Common disregard for system maintenance.
 "As the technical aptitude required to have a website drops," the webmaster is increasingly the weakest link. Sites running atop the top 4 CMS platform investigated by Securi were overwhelmingly out-of-date.
"As the technical aptitude required to have a website drops," the webmaster is increasingly the weakest link. Sites running atop the top 4 CMS platform investigated by Securi were overwhelmingly out-of-date."There is a sharp drop off in the knowledge required to have a website, which is breeding the wrong mindset with website owners." The report concludes, "One thing we know from this report is that vulnerable software is a big problem, contributing to a large number of compromises. The blanket guidance to stay current and update is falling on deaf ears."
Source: Securi Website Hacked Report 2016 - Q1
Subscribe to:
Posts (Atom)








